So you need to figure out the year of production for your Fender guitar or bass. You're not alone. Fenders rank as the most frequently bought and sold instruments on Reverb, and finding a precise date of manufacture can be key to determining the value and specifics of an instrument.
Speccy - find the details of your computer's specs. Download the latest version free. Software Informer; cnet Editor's Pick; Chip Online; PC World. Looking to download safe free versions of the latest software, freeware, shareware and demo programs from a reputable download site? Visit FileHippo today. Retrouver Serial Avec Ollydbg 2 there. Retrouver Serial Avec Ollydbg Tutorial Beginners. 0 Comments Read Now. Comment trouver le cl. Nitro PDF Pro 10 Crack Serial Key Plus Patch, Keygen provides other modern features such as magic sort and smart list. GameMaker: Studio's single codebase allows you to directly export your game to all supported platforms, reaching an unprecedented.
The most important thing to keep in mind when dating a Fender is the highly modular nature of the designs. Like Henry Ford, part of Leo Fender's genius was in optimizing the company's production efficiency. His guitars were built en masse by an entire factory, not a single luthier toiling over one instrument at a time. Features like bolt-on necks and pickups wired into the pickguard all helped the Fender factory churn out guitar after guitar, day after day. This also means that various parts used on a particular guitar may have come from different points in time, so no single number can absolutely define when the instrument was built.
Instead, the best approach to dating a Fender is to combine indicators from the design of the instrument, the dates found on the neck and body, along with the serial number. Once you have the information you need, if you're interested in selling your Fender, you can use Reverb to get it in front of the largest audience of musicians in the world by clicking on this link.
Design Changes and Features
Perhaps the best place to start when dating your Fender is to get an approximate idea of the era based on the instrument's design and components. This can be a tall order for someone less versed in guitar history, but we do have some resources here on Reverb to help you out.
For starters, there's the
We also have some other blog posts related to Fender that can hopefully be of some help. There's A Brief History of the Stratocaster Part I and Part II that follows the evolution of the most popular Fender guitar of all. Similarly, take a look at Behold the Jazzmaster for general timeline of the history of everyone's favorite offset guitar. For Fender during the turning point era of the mid-'60s, check out Fender and the CBS Takeover.
Body and Neck Dates
Through much of Fender's production history, Fender workers would print or write a production date on both bodies and necks where the two pieces meet. Xpand rally xtreme (pc iso download completo. These dates will tell when the original part was manufactured, but are not exact indicators of when the guitar was actually put together and finished.
Here is what the neck date and body date look like from a 1952 Telecaster:
If you're not comfortable removing the neck of a guitar to peek at the date marker, I encourage you to take it to a local tech or luthier.
I will also mention briefly pot-codes as a resource (numbers on the internal potentiometers of the guitar). These can definitely be useful in cases where no other numbers exist, but just tell when the pot itself was made. Who knows how long it was waiting in the Fender factory before finding its way into a Tele?
Serial Numbers
Like the body and neck dates, using serial numbers to date a Fender is not a sure bet. At many points in Fender's history, serial number usage overlapped again owing to the modular manner of production. Below we'll go into detail about the various serial number schemes employed by Fender as far back as 1950. There are certainly plenty of exceptions, so again, using serial numbers in conjunction with other dating methods is always the best bet.
Click on the links here to jump directly to the serial number style that matches your instrument:
The Early Years: 1950 - 1954
In the early years, Fender serial numbers schemes were specific to the model. Esquires, Broadcasters and Telecasters shared a serial number sequence, while the landmark Precision Bass had its own system. In this early period, the serial number can be found on the bridge of the instrument (see image).
Here are the rough serial number ranges for the early Esquires and Telecasters:
| 0001 to 0999 | 1950 - 1952 |
| 000 to 5300 | 1952 - 1954 |
And here are the ranges for the original Precision Basses:
| 161 to 357 | 1951 |
| 299 to 619 | 1952 |
| 0001 to 0160 | 1952 |
| 0161 to 0470 | 1951 - 1952 |
| 0475 to 0840 | 1952 - 1953 |
| 0848 to 1897 | 1953 - 1954 |
Also, for the first half or so of 1954, the inaugural run of Stratocasters had a distinct number sequence all under number 6000.
Classic Serial Numbers - 1954 - 1963
By mid-1954, Fender began using a universal serial number sequence for all its instruments. At this time, the location of the serial number also shifted from the bridge to the neckplate (the metal plate located on back of where the neck meets the body).
Here's how the serial numbers break down from 1954 to the beginning of 1963, though there are some areas of inconsistency in this era:
| 0001 to 7000 | 1954 |
| 7000 to 9000 | 1955 |
| 9000 to 17000 | 1956 |
| 17000 to 25000 | 1957 |
| 25000 to 34000 | 1958 |
| 34000 to 44000 | 1959 |
| 44000 to 59000 | 1960 |
| 59000 to 71000 | 1961 |
| 71000 to 93000 | 1962 |
| 93000 to 99999 | 1963 |
L Series - The Transition Period of 1963 to 1965
At the very end of 1962 and into 1963, Fender changed to a system where serial numbers began with an 'L.' According to some accounts, the L was supposed to just be a 1 to mark the cross over into the 100,000 range from the previous scheme, but an L was used by mistake.
Here the range of the L-series serial used each year. Some of the earliest ones actually popped up in late 1962 as well:
| 0L00001 to L20000 | 1963 |
| L20000 to L59000 | 1964 |
| L59000 to L99999 | 1965 |
F Series - CBS Era 1965 - 1976
After the CBS purchase of Fender in 1965, the factory switched to a new serial sequence with numbers that continued the same general format used prior to the takeover. These are generally referred to as F series due the large Fender branded F on the neckplates of the era. This period also saw a switch from the orginal four-bolt neckplate of the '60s to a three-bolt neckplate in just one example of cost-saving costs introduced under CBS.
| 100000 to 110000 | late 1965 |
| 110000 to 200000 | 1966 |
| 200000 to 210000 | 1967 |
| 210000 to 250000 | 1968 |
| 250000 to 280000 | 1969 |
| 280000 to 300000 | 1970 |
| 300000 to 340000 | 1971 |
| 340000 to 370000 | 1972 |
| 370000 to 520000 | 1973 |
| 500000 to 580000 | 1974 |
| 580000 to 690000 | 1975 |
| 690000 to 750000 | 1976 |
Post 1976
Starting in 1976, Fender transitioned to a new serial number scheme and moved the placement of most serial numbers to the headstock of the instrument. Depending on the era and model, the number can be found on either the front or back of the headstock.
After a short period of overlap with the old system, the post-76 numbers will start with a letter that indicates the decade, followed by a number that indicates the year of that decade. The decade letter codes break down like this: S = 1970s, E = 1980s, N = 1990s, Z = 2000s. In the 2000s, you'll also see serials starting with a DZ which indicates the Deluxe series, but the format is otherwise the same.
For example, a serial number with N4 would be from 1994. One starting with Z5 would be from 2005.
This scheme is not 100% consistent due to a number of production factors, such as Fender producing more serialized decals than needed in a given year. This is particularly pronounced in the transitional period of the mid-'80s, though the system has been pretty much on point since about 1990.
After 2009, the letter changed to a format starting with US then two digits that tell the year of the current decade.


Here's the breakdown of Post-1976 American-made Fender serials:
| 76 + 5 digits | 1976 |
| S6 + 5 digits | 1976 |
| S7 + 5 digits | 1977 - 1978 |
| S8 + 5 digits | 1978 |
| S9 + 5 digits | 1978 - 1979 |
| E0 + 5 digits | 1979 - 1981 |
| E1 + 5 digits | 1980 - 1982 |
| E2 + 5 digits | 1982 - 1983 |
| E3 + 5 digits | 1982 - 1985 |
| E4 + 5 digits | 1984 - 1988 |
| E8 + 5 digits | 1988 - 1989 |
| E9 + 5 digits | 1989 - 1990 |
| N9 + 5 digits | 1990 |
| N0 + 5 digits | 1990 - 1991 |
| N1 + 5 or 6 digits | 1991 - 1992 |
| N2 + 5 or 6 digits | 1992 - 1993 |
| N3 + 5 or 6 digits | 1993 - 1994 |
| N4 + 5 or 6 digits | 1994 - 1995 |
| N5 + 5 or 6 digits | 1995 - 1996 |
| N6 + 5 or 6 digits | 1996 - 1997 |
| N7 + 5 or 6 digits | 1997 - 1998 |
| N8 + 5 or 6 digits | 1998 - 1999 |
| N9 + 5 or 6 digits | 1999 - 2000 |
| Z0 + 5 or 6 digits | 2000 - 2001 |
| Z2 + 5 or 6 digits | 2001 - 2002 |
| Z3 + 5 or 6 digits | 2003 - 2004 |
| Z4 + 5 or 6 digits | 2004 - 2005 |
| Z5 + 5 or 6 digits | 2005 - 2006 |
| Z6 + 5 or 6 digits | 2006 - 2007 |
| Z7 + 5 or 6 digits | 2007 - 2008 |
| Z8 + 5 or 6 digits | 2008 - 2009 |
| Z9 + 5 or 6 digits | 2009 - 2010 |
| US10 + 6 digits | 2010 |
| US11 + 6 digits | 2011 |
| US12 + 6 digits | 2012 |
| US13 + 6 digits | 2013 |
| US14 + 6 digits | 2014 |
Signature Series
American-made signature series instruments follow a very similar scheme to the above, but use a prefix S before the decade letter. For example, a Signature Series guitar from 1998 would have a serial starting with SN8 followed by five digits.
American Vintage Reissue models
The major exception to all of this is the American Vintage Reissue (AVRI) series. These have serial numbers starting with V and do not strictly correlate to years. The neck dates on these guitars, however, are usually reliable.
Made in Japan Fender Serials
Fender Japan serial numbers can usually be found on the back of the neck near the neck joint. Though examples also exist with the number on the headstock or the neck-plate in the case of certain early reissue models. Up until 1997, the serial was paired with the words 'Made in Japan.'
In 1982, Fender expanded operations with a series of instruments produced in Japan by the Fuji Gen Gakki company. Like the US serial numbers, MIJ (made in Japan) serials start with a letter or pair of letters that indicate the rough year of production. This system, however, is notoriously inconsistent and incomplete, which makes dating by serial number even less reliable for MIJ Fenders.
Here's a breakdown of serials for the 'Made in Japan' era:
| JV + 5 digits | 1982 - 1984 |
| SQ + 5 digits | 1983 - 1984 |
| E + 6 digits | 1984 - 1987 |
| A + 6 digits | 1985 - 1986 |
| B + 6 digits | 1985 - 1986 |
| C + 6 digits | 1985 - 1986 |
| F + 6 digits | 1986 - 1987 |
| G + 6 digits | 1987 - 1988 |
| H + 6 digits | 1988 - 1989 |
| I + 6 digits | 1989 - 1990 |
| J + 6 digits | 1989 - 1990 |
| K + 6 digits | 1990 - 1991 |
| J + 6 digits | 1990 - 1991 |
| K + 6 digits | 1990 - 1991 |
| L + 6 digits | 1991 - 1992 |
| M + 6 digits | 1992 - 1993 |
| N + 6 digits | 1993 - 1994 |
| O + 6 digits | 1993 - 1994 |
| P + 6 digits | 1993 - 1994 |
| Q + 6 digits | 1993 - 1994 |
| S + 6 digits | 1994 - 1995 |
| T + 6 digits | 1994 - 1995 |
| U + 6 digits | 1995 - 1996 |
| N + 5 digits | 1995 - 1996 |
| V + 6 digits | 1996 - 1997 |
Crafted in Japan Serial Numbers
In 1997, Fender changed the 'Made in Japan' decal to say 'Crafted in Japan.' There is some overlap with the earlier 'MIJ' serials, so it's important to note if your instrument carries the 'Made in Japan' or 'Crafted in Japan' decal.
Here are the serial numbers for the 'Crafted in Japan' or 'CIJ' era:
| A + 6 digits | 1997 - 1998 |
| O + 6 digits | 1997 - 2000 |
| P + 6 digits | 1999 - 2002 |
| Q + 6 digits | 2002 - 2004 |
| R + 6 digits | 2004 - 2005 |
| S + 6 digits | 2006 - 2008 |
| T + 6 digits | 2007 - 2008 |
After 2007, Fender Japan switched back to marking Fenders as 'Made in Japan' though for a few years instruments with both decals were made. Serial numbers since this transition have continued the same sequence as the 'CIJ' era.
Made in Mexico Fender Serials
Fender opened a factory in Ensenada, Mexico in the late '80s and instruments started coming off the line in 1990. Mexican-made (MIM) Fenders carry a serial number on the headstock starting with an M. Some exceptions include a handful of special editions and signature models as well as the split US/Mexican-made California series which all have a 'AMXN' at the beginning of their serials.
The MIM serial number scheme is actually very straight-forward. For Mexican Fenders made in the 1990s, the serial will start with an MN followed by a number that indicates the year of the decade. Instruments made in the 2000s follow the same form but start with MZ. For the 2010s, the prefix is MX1. For example, a serial number starting with MN2 would be 1992.
Here's the serial number breakdown for a majority of MIM Fenders:
| MN0 + 5 or 6 digits | 1990 |
| MN1 + 5 or 6 digits | 1991 |
| MN2 + 5 or 6 digits | 1992 |
| MN3 + 5 or 6 digits | 1993 |
| MN4 + 5 or 6 digits | 1994 |
| MN5 + 5 or 6 digits | 1995 |
| MN6 + 5 or 6 digits | 1996 |
| MN7 + 5 or 6 digits | 1997 |
| MN8 + 5 or 6 digits | 1998 |
| MN9 + 5 or 6 digits | 1999 |
| MZ0 + 5 or 6 digits | 2000 |
| MZ1 + 5 or 6 digits | 2001 |
| MZ2 + 5 or 6 digits | 2002 |
| MZ3 + 5 or 6 digits | 2003 |
| MZ4 + 5 or 6 digits | 2004 |
| MZ5 + 5 or 6 digits | 2005 |
| MZ6 + 5 or 6 digits | 2006 |
| MZ7 + 5 or 6 digits | 2007 |
| MZ8 + 5 or 6 digits | 2008 |
| MZ9 + 5 or 6 digits | 2009 |
| MX10 + 6 digits | 2010 |
| MX11 + 6 digits | 2011 |
| MX12 + 6 digits | 2012 |
| MX13 + 6 digits | 2013 |
| MX14 + 6 digits | 2014 |
Exceptions
There are a number of exceptions to all these serial number schemes. As mentioned above, many reissue models use serial numbers that don't really correlate to their age. Additionally, there have been plenty of artist models, limited editions and other rare models that use a unique serial number. Examples include the 35th anniversary series, many of the uniquely finished Strats from the early '80s, as well as various export-specific models which carry a serial number starting with FN.
Again, the serial number alone in any of these cases is not definitive and the best approach is to combine that with other methods like the neck and body dates, as well as just the features of the specific instrument. If you have any questions as to what Fender you're dealing with, I encourage you to seek out a local guitar shop or luthier to help figure it out.
We understand the importance of online privacy and are committed to complying with the EU General Data Protection Regulation. To reflect our commitment, we updated our terms and conditions. By continuing to use Reverb, you agree to these updates, and to our cookie policy. Learn More
In the previous IDA Pro article, we took a look at the basics of reverse engineering source code and binary files. This rare dissertation committed to impart cracking and byte patching in a binary executable using IDA Pro with the intention of subverting various security constraints as well as generating or producing the latest modified version (Patched) of that particular binary. IDA Pro is typically utilized to analyze the disassembled code of a binary so that the internal mechanism could be comprehended and identify the inherent vulnerability in the source code.
This article comprises subsequent contents:
- Binary Sample
- Patching Configuration in IDA Pro
- Binary Analysis
- Binary Cracking & Patching with IDA Pro
- Script Patching Substitute
- Final Note
IDA Pro appears to have managed mystical potentials in the reverse engineer’s mind by having the impression that merely opening a binary with IDA will reveal all the secrets of a target file. IDA Pro is intended to assist you in considering the behavior of a binary by offering us disassembled code. IDA Pro is in fact not designed to modify or patch the binary code to suit your needs like other tools such as OllyDbg and CFF Explorer. It is really only a static-analysis disassembler tool. It can only facilitate your attempts to locate software vulnerabilities, bugs and loopholes which are typically utilized by both white hat and black hat professionals. Ultimately, it is up to your skills and how you apply them as to whether IDA makes your search for vulnerabilities easier.
Essential
This tutorial requires thorough knowledge of Assembly Programming and Hex Code manipulation because patching binary with IDA Pro especially deals with assembly opcode instructions. Besides that, the reverse engineer is supposed to operate the IDA Pro Software IDE features perfectly. This operation lists the following tools of the trade:
- The Target Binary (C /C++ code)
- IDA Pro Interactive Dissembler
- IDA-Script File (*.idc files)
- Assembly Language skills
- ASCII Converter
Ethical Hacking Training – Resources (InfoSec)
Binary Sample
This article exposes the demonstration of byte patching over a typical C++ binary which essentially required a user password to validate his identity and let him log into the system, and such confidential information is only provided to the registered person indeed. There is of course no direct method to breach into this application without being authenticated, except to reverse engineer or patch the critical bytes which are responsible for performing validation. The following code will make the binary executable live as binaryCrack.exe:
We can use any compiler to execute the aforementioned binary source code which makes an executable as binaryCrack.exe, and when we run that file, it will prompt to enter the password. If we enter the correct password as “ajay” then it shows the congratulations message, otherwise it will issue the wrong password message as following.
It is probable that we might not have the real password and in such circumstances we can’t proceed without this information. So the only option left is Reverse Engineering this binary and manipulating the sensitive bytes to suit our needs as we shall see in the next sections.
Patching Configuration in IDA Pro
The patching or editing assembly code features are normally invisible in the IDA Pro. You can double check from the Edit menu that no Patch program options appeared. Thus, in order make this option visible, open the idagui.cfg configuration file of IDA Pro which is located at Drive: Program FilesIDA PRO Advanced Editioncfg folder and scroll down to find the DISPLAY_PATCH_SUBMENU option which is typically set to NO. So, do the following changes and save this file.
After saving this file, re-launch the IDA PRO and the moment you change the submenu option in the configuration file, you can notice that Patch program option becomes visible in the Edit menu.
Now, load the target binary into IDA Pro. It will ask to create a new database as usual, then we select the PE file option as shown in the following figure. An important point to remember: don’t forget to uncheck the Make imports segment option, because some useful data can be lost from the database if this option is enabled.
The target file will be loaded into the IDA Pro, but we could still not modify the byte sequence of the binary file even if enabling the Patch program option in the Edit menu earlier. So here, the role of special IDA script files comes into light as they are able to modify the byte like OllyDbg as well as write the changes into the executable to make the effect permanent.
The IDC script files can be downloaded from this URL as http://www.openrce.org/downloads/details/57/PE_Scripts. When downloaded, extract the files in a separate folder on the file system of your machine. A few script files are provided, but mainly two script files are significant:
After loading the target binary into the IDA Pro, open the folder where the aforesaid IDA script files are located and execute the pe_sections.idc file in order to extend new functionality into IDA Pro such as binary patching and writing. You can ensure the new specification from the Segments (shift + F7) windows that certain new segments are automatically added.
After successfully completion of such aforesaid operations, we can modify as well as write the byte sequence into binary file.
Binary Analysis
We have only the binary executable and it is almost impossible to know about the logic implementation without the source code. But we can disassemble the source code of any binary by employing IDA Pro, because unless we are aware of logic flow, how can we subvert any security mechanism? Hence, let’s analyze the proper logic flow path of the binary file.
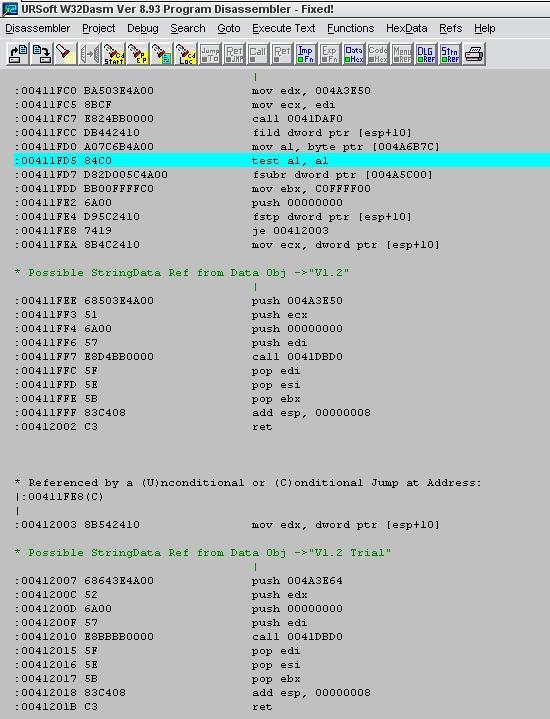
As we can consider the following image, IDA Pro disassembles the binary into raw assembly instruction sets. This program first prompts the user to enter the password by displaying a string message, then compares this value to a predefined value “ajay” which might be the real password. The comparison happens via string class strcmp method, and if the value is 0 then the entered value is correct; otherwise it is incorrect.
If the value of eax register is 1 then the execution is shifted towards the loc_411444 block by jnz statement, where the “wrong password” message would be echoed in the screen as follows:
And if the value of eax is 0 then jump won’t throw the execution anywhere. The program informs us that we have entered the correct password:
We can easily anticipate that the Jump instruction determines either the password is correct or incorrect. If the eax register has value 1 then execution is diverted towards the “wrong password” box flow, otherwise the “congratulations” message would be displayed. As we are implying from execution flow, everything depends on jnz instruction. So, a reverse engineer would surely be interested in this instruction because manipulation of this instruction can produce different results.
Binary Cracking and Patching
As we have concluded from the analysis, the outcome of this binary application is regulated by the jnz short 1oc_411444 statements. The 1oc_411444 instruction belongs to the unmatched password display block, and execution is directly jumped to this block, as you can notice by the RED arrow.
However, all we have to do is to change the corresponding jnz statement related bytes. So right click on the current location of this statement and synchronize it with Hex Editor View in order to examine this statement byte sequence:
The hex view offers a 16 bytes sequence in one line and each two bytes represent only one assembly instruction set such that the hex value 75 35 belongs to .text: 0041140D address location where assembly code jnz short 10c_411444 is implemented as following.
So we have to identify the correct bytes to the specific instructions so that we can modify them to suit our needs. The following figure showcasing the hex code refers to which instruction.
Finally, we have concluded that hex code 35 is the key value that directing the execution flow of the program. However, select the address location 0041140D into text view and go to Edit menu, choose Patch program and select Patch Bytes over there. It will show the entire 16 hex bytes sequence alike to hex view:
In order to diffuse the effect of the jnz statement where the execution is shifting towards the 1oc_411444 block, we have to change its corresponding hex value 35 to 00 which typically fills a nothing action in the memory.
The moment you change the 1oc_411444 instruction code to 00, it will also reflect in the assembly:
You can also notice the modification in the hex view: Find rapidshare files.
One of the important changes to notice is that after making the value 00, no jump arrow is showing, which was pointing the execution divert to 1oc_411444 earlier.
Now open the graph view and notice that the “congratulations” block is merged into the main code rather than being separated as before editing the hex value. The BLUE arrow finally goes to end of statement block and the “wrong password” block is isolated or disconnected from the main operation. So even if we enter wrong password value , always the correct password block would be executed because jnz statement code is diffused to 00 and the 1oc_411444 block is disconnected:
Okay, we have done the byte editing, so it’s time save the effect permanently into memory, but IDA Pro is not capable of writing bytes of the binary file into memory; instead it can write altered bytes into a database. So for this purpose, IDA special script file are used here. Go to File and select Script file and choose pe_write.idc which makes the perpetual effects in the memory:
The moment you run the pe_write.idc file, you will notice that bytes have been written to segments successfully, and lastly, IDA will prompt to re-save the binary file:
Save the modified binary with the same name as binaryCrack.exe:
Retrouver Serial Avec Ollydbg Guides
Now, load the binaryCrack.exe and it will prompt to enter the password, merely enter any value and BINGO!!!!!!! Congratulations message along with original password appearing. We have successfully bypassed or subverted the password mechanism by patching some related critical bytes using IDA Pro.
Patching String Bytes
As we can observe in the binaryCrack.exe, couples of strings messages are showing. We can access all these strings into place via String window (shift + F12) and can directly reach to its assembly code merely by clicking the string.
It is not a good programming practice to show the sensitive strings likes serial keys or passwords directly. Such information should be hidden because after patching (reverse engineering) the password’s assembly code, the hacker can easily aware that the password is “ajay” as it is showing after the “congratulations” message. So we can hide or rename the password on the screen by patching its corresponding bytes.
So, double click over the “ajay” in the String windows, and IDA will let us reach its assembly code where we can modify its visibility:
Thereafter open the Hex view and we can observe the “ajay” byte code sequence as 61 6A 61 79 00 as following:
Again open the Patch Bytes from the Patch program in the Edit menu and replace all these bytes with 00 as following:
Now once again, run the pe_write.idc to make changes perpetual in the binary file and the binaryCrack.exe. Enter any value as the password and observe that this time the real password is not showing:
Removing Segments
A question comes into mind: why should we display the string message after the “Congratulations” message when we subverted the password mechanism? We cannot execute a particular assembly code by using IDA Pro. Here, we can easily figure out that the code instruction after address location 00411411 is senseless to be displayed as:
This time we are not patching the bytes, instead we are integrating new assembly code so that any string message won’t display after the “Congratulations” message. Hence, go to Patch program and choose Assemble as following:
Now place nop assembly instruction which stands for no operation and it decides that none of the code would be executed as following:
After this, you can notice that nop is placed after 0041132 locations:
Now, run pe_write.idc again and notice that none of code is executing after the message:
Script Patching Substitute
It is not necessary that we only patch bytes by using the IDA Script file which exports the current IDA’s database into the EXE binary executable. Rather, we can opt for another approach. First make changes in the byte or hex code just by editing them and produce a new DIF file as test.dif. Now open the test.dif file and it shows the original hex code and patched code:
Later compile the following C program by using any editor (I suggest use GCC in the linux platform).
After compiling this code successfully, execute the following command on DOS which requires the DIF file and new patched file name as:
Retrouver Serial Avec Ollydbg Guidelines
ida_patcher.exe -i PatchedApp.exe -p binaryCrackPatched.dif
This approach also fulfills the same objective and produces a patched binary as defined earlier in the papers.
Final Note
Trouver Serial Avec Ollydbg Guide
So, we have learnt one of the amazing tactics of patching the binary and producing new executable files using IDA Pro, for which crackers used to struggle because as of the IDA limitation, it can only disassemble the binary code to analyze the vulnerabilities or bugs in the code. We can temporary divert the instruction code by modifying the ZF register during debugging just by placing the breakpoint, but can’t patch or modify the bytes sequence into the memory directly to produce new binary executable, because IDA Pro makes change in the database, not in the binary executable. This paper taught us how to make visible the hidden features of the Patch program in IDA Pro IDE. We have also come across with string patching and new way to modify bytes by producing DIF file, which later passed as an argument to a custom C patch code.